Review Of 3 Of The Leading Virus Scan Programs
Review Of 3 Of The Leading Virus Scan Programs
Blog Article
The tablet needs to be light. It would be impossible to invent a tablet that is featherweight, at least in this century. An extremely light Amazon tablet would be extremely simple to carry.
Among the first Windows Vista misconceptions is that it really has about as much security as Windows XP that has Service Pack 2 set up on it. While I do not desire to undermine the total, security features of Windows XP, as there are some very good security steps in location for this os. Windows Vistas security is completely reorganized and provides numerous benefits in the area of security that XP merely does not have in location. Examples of these enhancements consist of that of the "User Account Control", or "UAC", and even the ability to operate and run Internet Explorer 7 on a safe and secure basis. The Windows Firewall software is also more boosted in Vista therefore keeping it more safe and secure.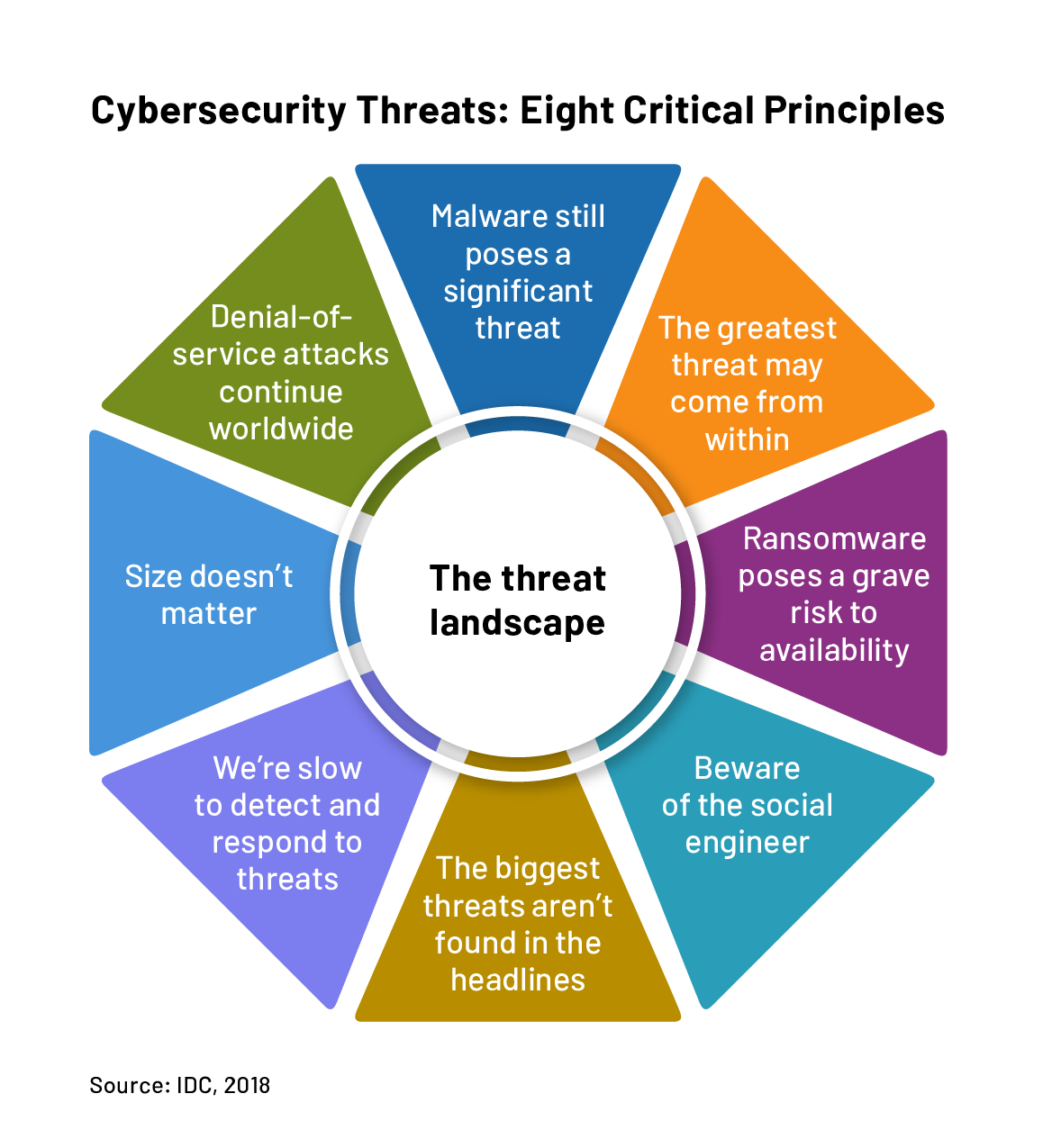
4) What is the business's history? The longer they have stayed in business, the more they have actually found out how to respond to the latest trends, or even better see them coming before they take place. Wrongdoers are always making modifications; they must be, too.
Basically virtual racks are personal, dedicated Cybersecurity Threats networks. They're commonly used by companies thatkeep a lot and gather of delicate customer data like credit card numbers and names - a commodity in the cracker world.
For a moment, let's think about your diet as a type of game. What I have discovered in my research is that you are most likely playing the wrong diet plan video game. It's likely you are playing the drop weight game rather of the stay on a diet video game, while your body plays a completely various game called the survival game.
Beware of online scammers. I understand a guy in Barbados who works for a prominent worldwide company and is abusing his authority to send me scam emails apparently from the FBI. I pity him because of his jealousy of my success, but that goes to reveal you the calibre of people dealing in cybercrime. They're much more advanced than the dodgy, antisocial geeks Hollywood likes cybersecurity threats to make us consider them as. When it concerns online scams, prevention is the only way. Don't reply, that simply makes them clever about figuring out your behaviour, unless you want them to consider you as a particular type. XD As a rule of thumb, delete any mail you do not anticipate. Don't even preview it. That just fires up your temptation. Simply erase it after you have marked it in your inbox as phishing fraud.
The leading technique of removal is downloading one of the very best antivirus programs on the net that is particularly tailored to eliminate these types of hazards. I have actually found one that performs deep registry scans in locations where the virus hangs out. The program also uses actual time protection to avoid future attacks like the Windows Security Center caution. Scan your computer for free listed below and see what type of dangerous infections are prowling on your system.
Report this page